The Cyberspace challenge for the CISO
Our lives are immersed in the information society and interconnection. We need quality information with security features that contribute confidence to decision-making. This is true for all areas of society: education, economy, industry and particularly for the Information Technology (IT) sector.
Cyberspace is the new corporate perimeter. In 2010, the US recognized, through Secretary of Defense William J. Lynn, that a new area for war existed beyond the four classic battlegrounds: land, sea, air and space: Cyberspace. According to standard ISO/IEC 27032:2012 Information technology - Security techniques - Guidelines for cybersecurity, this is defined as the “complex environment resulting from the interaction of people, software and services on the Internet by means of technology devices and networks connected to it, which does not exist in any physical form".
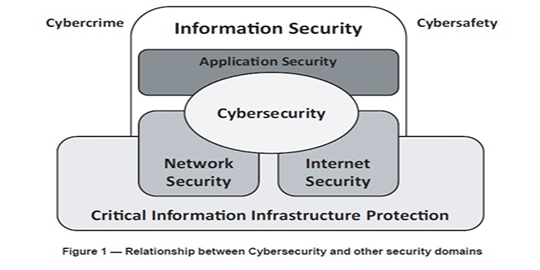
Cyberspace is complex as it requires the convergence of different types of security. The standard one highlights the relationships between Cybersecurity and other security domains. If we do without the nuances and labels of different security types, in my opinion we can focus on the idea: “security to generate confidence for services and operations”. This could be translated as the need to converge and align all securities in the same direction to concentrate risk processing synergies.
The complexity of Cyberspace and its implications may be understood, for example, from the perspective of critical infrastructures. Some of these, such as water or transportation, may not directly or significantly impact the status of Cybersecurity, in general. However, to the contrary, the lack of Cybersecurity may negatively impact the availability of critical infrastructure information systems while, likewise, Cyberspace is greatly dependent on the health and confidence of some critical infrastructure services, such as telecommunications.
From an organizational perspective, what actions are necessary to protect Cyberspace? To guarantee the Cyberspace is in good health, we must do what humans have always done since we climbed down from the trees of the African steppes: we need to know what occurs in our environment, what we define as “who”, “how”, “where”, “when” and “why”. As is the case for any primate, we need to know that the watering hole is free of predators and that the smoke from the fire indicates that, for the time being, the wind does not blow in our direction.
This means that we must be capable of gathering and processing trustworthy information that allows us to make correct assumptions.
The second step for the CISO is to mature as regards security information control. No doubt we have made progress, evolved and improved diverse aspects of security governance and management, but there is still an aspect concerning Information Technology that requires development: ”Cybersecurity intelligence”. In the interconnected world that draws closer, in which distances and speeds are measured in clicks of the mouse, it is necessary to have foresight and establish those controls that allow us to anticipate the materialization of its threats, trends and possible vulnerabilities that can be exploited.
Given that cyberspace belong to everyone, its protection will require a public-private framework with clearly established roles and responsibilities to allow, develop and articulate three key pillars for cooperation: information-sharing, the response to attacks, and intelligence for supporting, in addition, socioeconomic aspects, and not solely Cybersecurity.
To strengthen this framework, we need a fourth line of defense. In January 2013, the Institute of Internal Auditors (IIA) presented the concept of three lines of defense to help organizations with corporate risk management.

In this model, the first line of defense (IT operation functions) would implement the policies and standards responsible for monitoring processes. In the second line of defense, the organization of the CISO is responsible for managing tasks that guarantee proper network and infrastructure monitoring, reporting and follow-up of IT operations. The third line of defense, internal audit, is responsible for assuring that the first and second function as expected.
However, Cyberspace security requires a transversal or supporting fourth line of defense, based on something which already exists in our systems, but which we fail to exploit to its full potential: “Intelligence”.
How can we build a line of defense in Cyberspace? In principle, the CISO should contribute and, if necessary, exploit all the relevant data that passes through the information systems as well as that which is available in our immediate (or broader) environment for the purpose of defining and establishing the strategic requirements for the organization's security to set forth, at least:
- A behavior pattern for our organization.
- A logic for the deviations from this pattern.
- A response to either recover or change the status of the pattern, or avoid the sources of the deviation.
As of this point, we would be sufficiently self-aware to be able to share information and align strategies within a public-private framework of the Public Sector and organizations.
Fortunately, our starting point is not zero. “Intelligence” is inherent to human beings, despite the fact that sometimes our use of it fails to be methodological. We process the information we gather from our environment in such an immediate and innate manner, in such a seemingly natural way as regards our behavior, that we consider the result of our decision-making as based on “intuition” or, in more scientific terms, as filters applied by our brain's Reticular Activating System (RAS) that allows us to subconsciously filter and process tremendous amounts of information received. This is what enables us to focus our attention on issues we are concerned about or which worry us, like when we think of the color hot pink and suddenly start seeing it everywhere.
The military and government are ahead of us, as these sectors have historically applied a more methodological approach to the use of “Intelligence”. Proof of this is the publication in October 2013 by the US Department of Defense (DoD) of the document “Joint Publication (JP) 2-0 Joint Intelligence” (source: http://www.fas.org/irp/doddir/dod/jp2_0.pdf). This document proposes a life cycle model with six characteristics for the operation of intelligence which would help the CISO to complement security management (as well as IT and corporate management). The application of this model (or another to be adopted or adapted) would allow this fourth line of defense to strengthen security while complementing and supporting other areas of the organization that require strategic operational support.
The challenge of the CISO lays in making it possible for one's organization to be permeable to the need for gathering, comparing, analyzing and disseminating security information (and perhaps, furthermore, that of another nature, such as economic, or research-related, for its strategic use by the organization).
The Cyberspace security strategy will lead the CISO to a watch over what occurs on the horizon and/or in the immediate surroundings of the watering hole. Yet, this task may not be carried out in isolation, not when there exists a public-private relationship which still needs to be developed and organized and which will demand the information that passes through our systems. Information that must be processed and evaluated for use in more strategic, national goals and which, once disseminated, may be integrated within our knowledge base for understanding the direction of the wind and to be able to confide in the security of our environment.