Justin Bieber is only 23 years old, yet during his lifetime "humanity has burned up 41% of all the fossil fuels consumed in the planet's history”. With such discouraging news, it is no doubt necessary to take action against climate change and attempt to mitigate its effects before 2050.


From January 25 to 27 the University of Alcalá de Henares (UAH) played host to the 3rd Security and Cyber Defense Conference. On Monday Jan 25 we began our collaboration with CIBERSEG by offering a hacking workshop, followed by a Capture the Flag competition on iPhalanx, our cybersecurity training platform. A CTF (Capture the Flag) is a security competition in which the participants play an active role in a system and have to apply their security knowledge and other skills to solve the challenges posed.
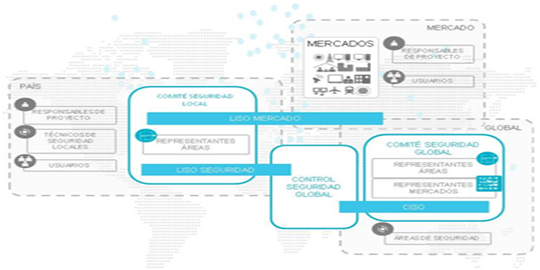
Divide and conquer. Julius Caesar's quote from ancient times proposes the most efficient way to confront complex situations and settings. However, when referring to security, we must do this through a holistic vision, where the whole is more than the sum of the parts. To this end, we must not forget that the ultimate goal of implementing adequate security controls, whether Information Security or of any other type, is merely to uphold the correct functioning of an organization so that it may wage its battle another day.
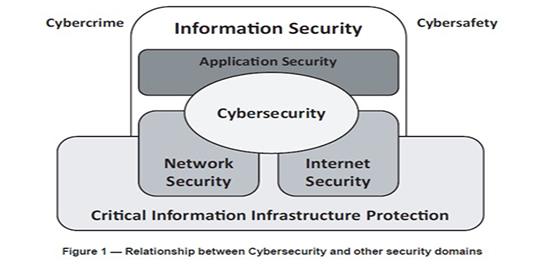
Our lives are immersed in the information society and interconnection. We need quality information with security features that contribute confidence to decision-making. This is true for all areas of society: education, economy, industry and particularly for the Information Technology (IT) sector.

If you did not read the first part of this article yet, I recommend you do it first. The second part is more complex and entertaining.
Below we will describe Bayesian Networks applied to Cybersecurity matters, without a doubt, one of the subjects I have been hooked in last months.
Bayesian Belief Networks

I've heard that this Saturday November 30 is International Cybersecurity Day or, same thing, Information Security Day. I'm sure that right now the three or four readers of this blog (and I'm including my four-year-old son) are Googling it (my son as well) to check it out and have come across other days like April 6. In any case, this celebration is a good time (and I'm being serious now) to review one of the most important yet least acknowledged aspects of our modern times, which is cybersecurity training.

One of the subjects included in my doctoral program "Information, Knowledge and Information", belonging to department of Computer Science at UAH, was called if I remember correctly “Computational Treatment Of Uncertainty”.


Following the summer break, we are back with a new post in the series on National Cyber Security Strategies, focusing this time on their objectives.
The cyber security objectives set by countries, as defined in their NCSS (National Cyber Security Strategies), all adopt a very similar pattern and can broadly be grouped as follows:

Since the end of last year, material facts have been produced in Spain that have resulted in tangible advancements in this field. This is just the start and the model must continue to mature progressively.
The first key milestone to take place after November was the publication, in mid December, of the National Cybersecurity Strategy (ECSN) in which various actions are proposed to ensure the Protection of Technological Equity in Spain, and which explicitly mentions the importance of protecting Vital Infrastructures among its objectives.
- 1
- 2
- 3
- 4
- siguiente ›
- última »
